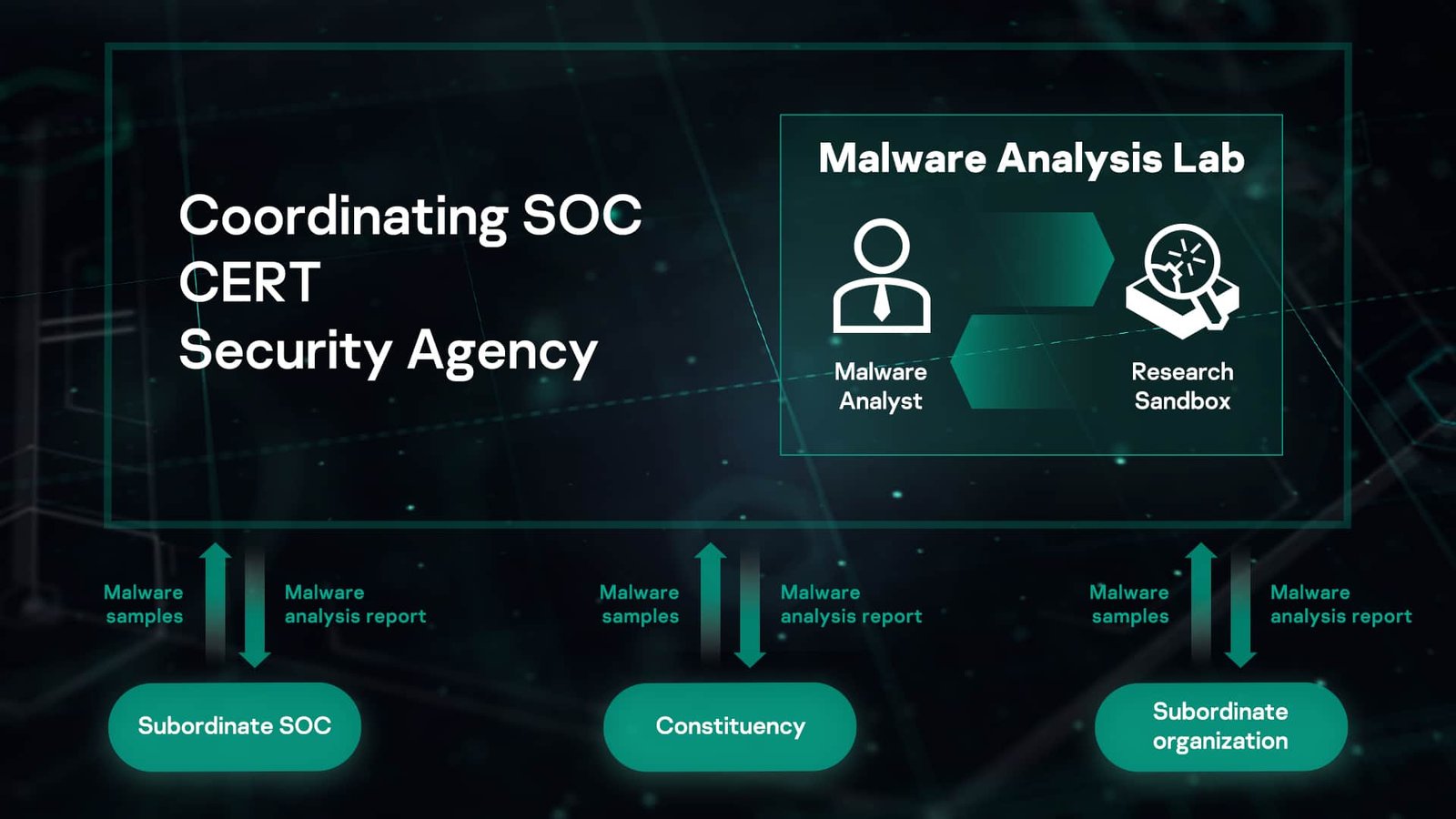
Malware labs : detection and analysis of cyber threats
Malwares obtain access to your private computers interrupting your machine activity and getting hold of your private information. Malwares does not include a software which causes unintended harm due to its insufficiency and they are characterised by its malicious intent which works against the user’s specification. Moreover, malwares gather personal information without taking the consent of the owner, gaining access to the operating systems and network resources as a result the computer operations are disturbed. Before going into detection and analysis of cyber threats it is mandatory to understand the classification of malwares. Malware comes in a wide range of variations like worm, virus, botnet, spyware and adware. Once they enter the system they replicate, hide and disable host’s privacy and protection. Malware lab after they are installed they are connected to their command and control servers for further instructions, which involves stealing data, infect other machines and allow inspection. We will discuss few techniques for detecting and analysing the malware executables hence providing comprehensive surveys on techniques and tools for detecting and analysing malwares.
Malware classification
Malwares are classified into various categories for example computer worms spread across the internet by reproducing itself on computers through their networks. The viruses and worms can carry a malicious design to do some damage. Furthermore, scammers use a wide range of tricks to get their spyware and key loggers loaded on to your computers. The malwares need to be analysed to understand the risks and intentions associated with it. The harmful program and its capabilities can be examined by executing it in a safe atmosphere. Moreover, few methods can be used for analysing a malware. For example analysing malicious software without executing it is called static analysis. The binary file has to be unpacked and unravelled before doing static analysis. The static analysis becomes very expensive and unreliable when malware binaries are modified into self flattened and uniquely structured binary files which are designed to resist reverse engineering.
Dynamic analysis
Unfinity Shock Lands involves analysing the behaviour of malicious code while before executing the malware lab samples the suitable monitoring tools are installed and activated. On contrary, another useful tool for analysing webpages containing malicious code is know as malzilla tool. This tool has the option of switching the user agents and picking the user referrer. It also have some proxy features and complex decoders all in one program.
Conclusion
Briefly discussed about the detection and analysis of cyber threats and how malwares are detected and analysed. Since most of the current surveys concentrate on a specific set of model this piece of article offers an in-depth study of methods to identify and evaluate malware with a clear understanding of domain specific analytics. Moreover, malwares when not dealt with precision and accuracy could harm files. Most users are worried about their personal information being exposed to the external threats and the tools we have discussed above are very helpful in determining the severity of attacks thus making it difficult for the malwares to get access to your personal information.